QR Code Phishing
Cybersecurity professionals have observed an increasing number of phishing attacks using QR codes (also known as Qshing). These malicious campaigns can bypass some email filters that rely on static or dynamic analysis of message content.
Unlike conventional phishing attacks, QR codes require the victim to scan the image with a mobile device. This requirement forces the victim to use an additional device that may not be as secure.
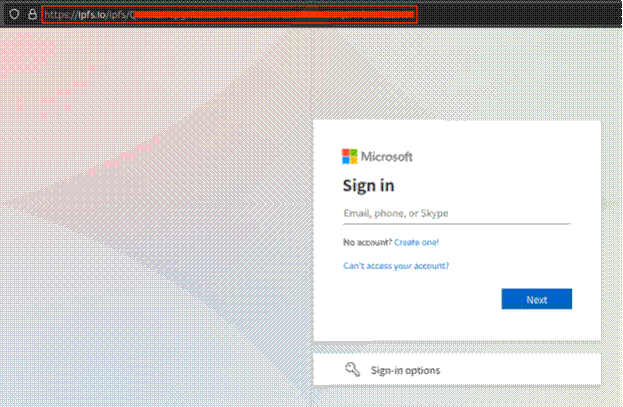
Without getting overly technical, cybercriminals can send users a phishing email containing a PDF attachment. The PDF includes a QR code that directs victims to a malicious URL, which steals session tokens and redirects to a page that hosts a malicious sign-in page to harvest Microsoft account credentials.
From there, the victim’s Microsoft 365 account is compromised.
Ways to combat this: make sure your organization is using a good email security and spam filtering tool, and consider investing in security training for your staff. And users should be reminded to always, always be wary of where they are entering login credentials. Remember, the majority of network compromises happen as a result of human error by a staff member.
Image: PDF email attachment containing a QR code directing users to a malicious phishing site. (Source: Secureworks)
Image: Malicious Microsoft sign-in page hosted on an IPFS gateway. (Source: Secureworks)